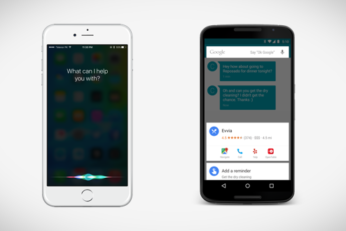
It seems that a day or two can't go by at the moment without another security researcher or research company finding vulnerabilities in the world's leading mobile platforms. Two security researchers who have been undertaking work on behalf of the French government have discovered a new clever way for hackers to gain control of an iOS or Android device by tapping into the platform's digital assistants, Siri and Google Now.
A new strain of malicious mobile adware has yet again been discovered, and it seems to have the potential to cause some serious damage to any device that it sinks its teeth into. It seems that rarely a day or two can pass by at the minute without us hearing about a new form of infection on one of the world's most popular mobile operating system. Some are extremely malicious and can do serious damage, some are less so. This newly discovered strain, dubbed Kemoge, falls under the former category due to its ability to gain full access to the infected device.
When you think of Apple devices and software, such as iPhones and iPads that run iOS, and Mac computers that run OS X from a security perspective, you tend to think on the more positive side. After all, Mac computers and iOS-powered devices are as secure as can be, right? Recent discoveries have shown that iOS isn't as secured as consumers may have hoped, and now a newly discovered exploit in OS X has revealed that it's possible to bypass Apple's Gatekeeper protection to install malicious apps without a user's consent.
Apple has taken the opportunity to provide some additional information about a number of third-party iOS apps that were recently discovered to be infected with the XcodeGhost malware. After the existence of the XcodeGhost trojan filtered down into the public domain, Apple took a number of steps to not only combat the issue, but also provide clarification on what it means to users, developers, and how it plans to rectify the problem and ensure that it doesn't happen again. Now, as an addendum to that info, the Cupertino-based company has listed the top 25 apps that have been affected by the malware.
As we reported recently, Apple's App Store was a victim of a large-scale attack, infecting a bunch of iPhone and iPad apps, mostly from China, with malware.
It is becoming increasingly rare for few days to pass by without us hearing about yet another malicious Android app that is loaded with ransomware, and sent out into the wild to wreak havoc amongst unsuspecting users. Just a few days back we heard about a ransomware which communicated over XMPP, and now a new strain, being dubbed Android/Lockerpin.A, appears to be taking things to a higher, more sophisticated level, by setting or resetting the PIN that is required to grant access to the Android device. Device owners are then forced to perform a factory reset and wipe all data from the device, or shell out $500 to the malicious individuals operating the malware, which is the really the standard course of action now.
A new strain of Android ransomware, which disguises itself as a legitimate application, has been discovered to be utilizing the Extensible Messaging and Presence Protocol (XMPP) for instant messaging, to receive commands and to communicate remotely with the server that controls the malicious installation.
Lenovo has gained a lot of fame recently for making quality laptops, among other things. However, a recently-uncovered "feature" in its laptops, allows Lenovo to install their own software on the laptops - without the user's permission and/or knowledge - even if a clean install has been performed using a Windows DVD or flash disk.
A new type of malware attack is on the loose, taking advantage of the recent Windows 10 release to spread its reach far and wide. According to a blog post by Cisco security researcher Nick Biasini, the attackers are using Microsoft's latest version of Windows as a way of getting people to install the malware, which then goes off and wreaks havoc.
Security researchers at Trend Micro have discovered a new vulnerability that they claim is present in Android 4.3 Jelly Bean up to the latest Android 5.1.1 Lollipop, which constitute to almost half of the Android devices out there. The vulnerability, if and when exploited, could make your device silent, unable to make phone calls and completely unusable. This apparently is caused by the way Android handles media files.