A new OS X malware uses standard extensions such as .pdf and .doc to disguise malicious files as basic, harmless subjects. Discovered by F-Secure, the spoof technique uses a special Unicode character found in file names that gives an app the appearance of a standard document file, and although the threat level is quite low at this point, any malware and outbreak should be treated with a dose of respect and vigilance.
OS X has long since been regarded as a safe haven, free from the malware and Trojan attacks that have plagued the Windows operating system over the years. However, Apple’s claim on its website that Macs weren’t susceptible to such problems had to be hastily removed in light of last year’s Flashback Trojan outbreak, and incidentally enough, F-Secure was at the heart of the clean-up job back then.

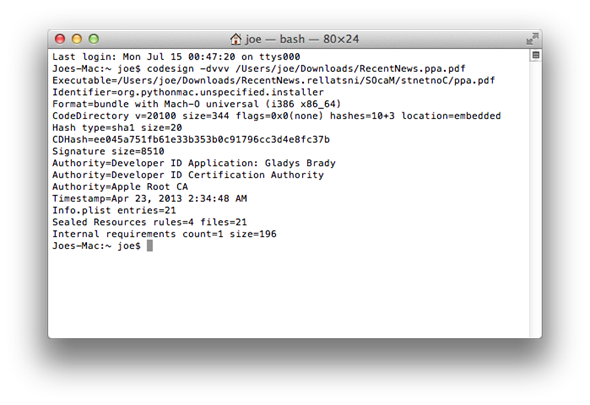
The new malware can, F-Secure has noted, open up disguised as a PDF document before creating a "cron" entry, capable of automatically launching Python scripts that in turn will try to connect to remote servers. When a successful connection to these servers is made, it the malware will attempt to upload screenshots and audio snippets that can, as you would imagine, be used for unscrupulous ends.
The chances of falling foul of this method would seem small indeed, particularly for those running the Gatekeeper feature which only authorizes the running of App Store-sourced apps. With that said, F-Secure has suggested that the spoofing technique has been found in malware signed with a valid Apple developer ID, so it’s certainly not something to be taken with a pinch of salt.
As Gatekeeper revokes the Apple developer ID in question, Gatekeeper will flag the program as having issues. So long as Apple stays on top of this, Gatekeeper should do as it purports in offering adequate protection against infiltration. By heading over to the Security & Privacy system preferences with OS X and setting Gatekeeper to only allow programs from the Mac App Store you can take a more proactive stance and stave off any potential threat from ‘legitimate’ Apple Developer IDs.
Although not on the scale of Flashback, the new malware, which F-Secure has dubbed Backdoor:Python/Janicab.A, serves as a reminder that no platform is entirely safe, and that everybody should remain cautious when using any kind of software.
(Source: F-Secure)
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the Web.

