A firm specializing in advising on information security has published a report into a vulnerability found within a component known as NetUSB, a proprietary technology found within millions of home routers around the world. NetUSB is developed by a Taiwanese company called KCodes and is essentially offered as a means of allowing PCs and Macs to connect to USB devices over a network. The bug within the technology, if exploited, could essentially allow malicious individuals to compromise any device running the driver.
NetUSB is an especially important part of the technology compound found within home routers due to its ability to offer “USB over IP.” Any USB device, such as a printer, external hard drive, or a flash drive, can be plugged directly into a router or access point containing the KCode software and is immediately made available through the network using a Linux kernel driver. In its simplest form it essentially utilizes the client side of the software available for Windows and OS X to simulate the experience of having a device plugged in locally using USB.

According to the write-up by SEC Consult, the issue within the software lies in the driver on the router-side of the equation, and is essentially a relatively simple buffer overflow problem that is not only a nostalgic throwback to the 1990s but is more concerning in the fact that we really don’t see these types of issues these days. As part of the communication process between the client and the server, the client side sends the name of the computer to the software on the server side. The concerning part is that if the name of the sent machine is longer than 64 bytes then it produces a buffer overflow, an issue that SEC Consult says can be exploited by malicious individuals to crash the router using a denial of service attack, or even worse, execute remote code.
The security company also found that the affected NetUSB drivers are installed in a number of extremely popular routers, including those made by D-Link, Netgear, TP-Link and ZyXEL. Whether or not the issue exists in all of these routers is another matter as some nay not actually have the affected drivers running. Still, it makes the Internet of Things seem like a terrible idea, right?
The complete list of affected routers is as follows:
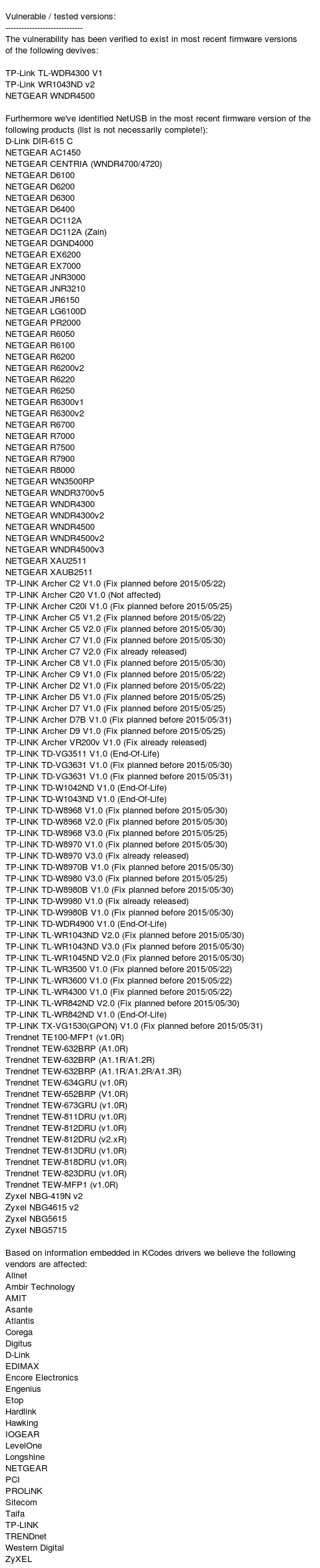
(Source: SECConsult)
You may also like to check out:
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the web.

