Android is not new to news of security bugs and vulnerabilities, but continues to roll on in spite of such news. Just recently, Rafay Baloch of RBH discovered a vulnerability in Android’s stock browser, including all browsers based on the stock AOSP code. This vulnerability was a serious one which caused the browser to fail in enforcing the Same Origin Policy (SOP) protocol, which basically governs how content from multiple resources is securely loaded into the browser. While this issue plagued pre-KitKat devices, Google was quick in patching it up. However, given the nature of Android’s ecosystem, updates aren’t rolled out that quickly, resulting in almost 45% Android devices out there that remain vulnerable according to the security experts at Lookout. Please note that this data is based on their apps user-base that is over 100 million, so it does make an interesting case nonetheless.
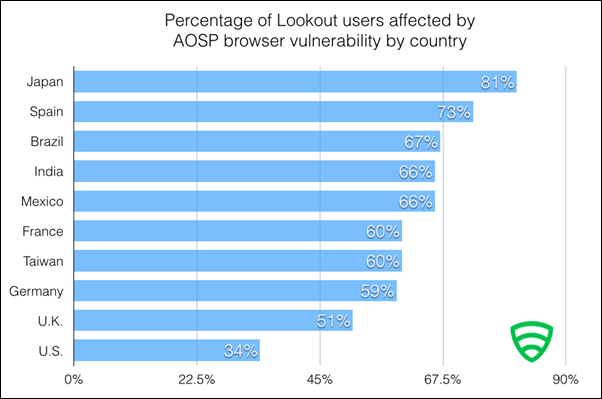
According to Lookout, this vulnerability is increasingly susceptible to an SOP enforcement failure in countries that do not receive updates as frequently, as say the United States, where 37% users at risk as compared to 81% in Japan.

While Google has patched up the vulnerability with an update, that still leaves a huge chunk of users waiting for Android’s ecosystem to speed it up a bit. Lookout however, recommends a few steps that vulnerable users can take to make their browsing experience safer:
- Upgrade your Android OS to version 4.4 or later. Anything older than 4.4 will be vulnerable.
- If you cannot upgrade your OS, I believe it is time to pick up a newer device supporting Android 4.4 or later.
- Download and install the new Chrome or Firefox browser, which are modern day browsers and are invulnerable to this bug.
- That done, make sure to set one of these browsers as a default one, so that all links on your phone open in either Chrome or Firefox.
According to folks at Lookout, the issue is a “glaringly obvious one“. This is what they had to say:
The same-origin policy (SOP) is a cornerstone of web browser security. It states that scripts on one domain are only able to interact with data from that domain, not any others. To understand this, take the example of a web page that loads content from more than one website onto one page. For example, a website that pulls Facebook data into the webpage you’re visiting. Depending on what websites are being intermingled, you might mix one untrusted site and another sensitive website (such as your email). If the SOP is working correctly, the untrusted site must “play in its own sandbox” and cannot access any sensitive data from the user’s webmail. However, if the untrusted site can somehow bypass SOP, it is able to interact with the DOM of the trusted site, and read or even send email as the user.
So there you have it, another bad day in the world of Android. But as noted above, there are ways to get around it, but unfortunately for some users running older hardware that don’t support KitKat, they are out of luck. But still, you can always go for a custom KitKat ROM, a perk every Android user has been enjoying for a long time now.
We just hope Google addresses this issue for everyone soon before matters get worse.
(Source: Lookout)
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the web.

