Turn away now if you’re an Android smartphone user with a nervous disposition that has only been made worse with the recent spate of vulnerabilities within Google’s OS that have become public knowledge. A number of security researchers from Israel have yet more bad news for Android device owners after discovering a bug that could potentially allow malicious individuals to take control of an unwitting device through the distribution of a solitary text message. What’s even worse, is that unlike previously discovered Android vulnerabilities, this one doesn’t come with a simple fix.
There’s no better time or place than the annually held Black Hat Security Conference in Las Vegas to learn about vulnerabilities and potential flaws in popular operating systems. The latest bug to be found within Android, which incidentally has been given the name “Certifi-gate“, is extremely similar to a previously discovered bug that surfaced at the back end of last month, but differs in the fact that this issue is slightly more complicated due to the fact that it relates to how Android verifies – or doesn’t verify in this instance – installed apps with privilege permissions.

The specific apps outlined in the presentation by the Israeli team from Check Point Software Technologies are often referred to as mobile remote support tools, or mRST if you’re into abbreviated terms. Those specific applications are often used by assisting teams to provide remote based support when and if it’s required. Due to the fact that Google doesn’t ship Android with these apps installed – they are often added at a later date by carriers and manufacturers – and are not susceptible to verification of authenticity certificates even though the applications have elevated system privileges. That’s where things start to go wrong.
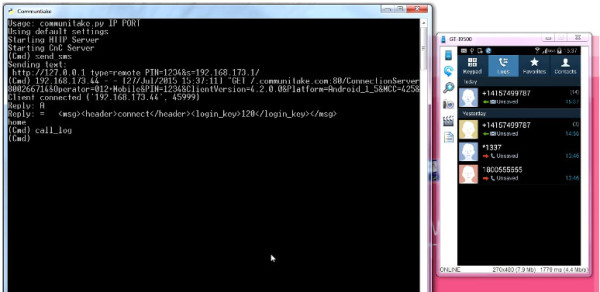
The immediate concern for Android users is that Check Point’s Ohad Bobrov, Avi Bashan et al have discovered a couple of relatively simple methods of spoofing certificates that can trick the mobile remote support tool for gaining almost unrestricted access to the target device. One method involved installing an innocuous looking flashlight application that requested only limited access to the device but was able to exploit the vulnerability to get full access. The second was via a seemingly innocent text message that had the capabilities of taking over the smartphone by triggering the remote access tool to issue a command.
Because the Black Hat Security Conference is all about discovering, sharing and ultimately fixing bugs, this one has already been addressed by Google and a number of device manufacturers. However, there are plenty of devices out in the wild that have yet to receive an update to fix this issue, and continue to remain vulnerable.
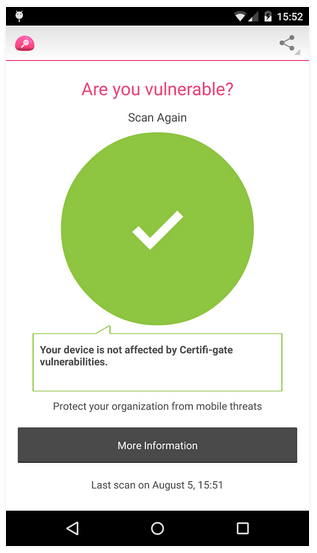
With that said, the team at Check Point have released an app called Certifi-gate Scanner on Google Play, with the purpose of helping users discover if their device is vulnerable to the exploits outlined here. You can download the app from here and check whether your phone is vulnerable to this hack or not.
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the web.

