While Android continues to go from strength to strength in offering consumers a better all-round user experience, there are still some noteworthy trade-offs when comparing with the likes of iOS. Malware remains a significant issue on Google’s mobile operating system, and with this week being the week of the Black Hat Security conference, new threats and possible solutions pertaining to Android security have been coming to light. One, outlined by Director of Kindsight Security Labs Kevin McNamee, involves the installation of a malicious app by the name of SpyPhone, which, once it infiltrates your device, can essentially keep tabs on all of your activity.
Android malware is fairly uncommon in the grand scheme of things, but when compared with the relatively incident-free iOS, does not make for particularly reassuring reading.

SpyPhone is a lot more prevalent in Android devices than some would give it credit for, with a recent sample of 500,000 devices by Lacoon Mobile Security showing as many as 1 in 800 were infected by this malicious software. While the software is commercial and used for all manner of purposes from nations spying to parental monitoring, McNamee and his team have written a special code enabling it to be concealed within any app.
So a perfectly legitimate Instagram or Cut The Rope APK could be manipulated to enable a hacker to spy on pretty much any aspect of your device. The code forces the app to request all permissions, leaving it with free reign of your contacts, messages, emails – you name it.
It’s rather unnerving to think how easily an intruder could get into your device’s innards by simply repackaging a common app, and whilst sticking to the Google Play Store while also making sure to check for unnecessary permission requests from basic apps will probably see you home and dry, there’s no doubt that SpyPhone is one to be keeping an eye out for.
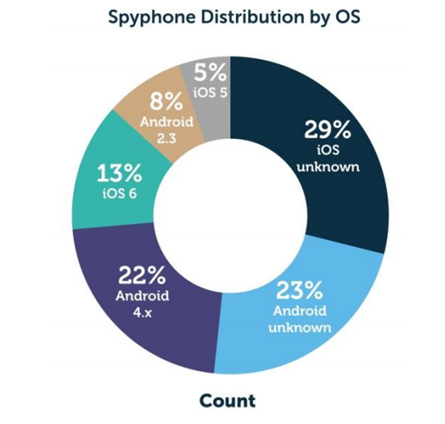
The fact that it operates completely silently is perhaps the most disconcerting aspect of all, so if you were to unwittingly install SpyPhone on your Android device, you’d no way of knowing anything was amiss until, say, your bank account was cleaned out, or worse, your identity completely taken away.
An intruder would have much more luck getting their unscrupulously repackaged app into circulation by distributing it outside of the Play Store, since Google’s monitoring channels should pick up on a hidden SpyPhone app. With that said, it’s not beyond the realms of belief that such an app could slip through the net, so always be sure to check for when apps appear to be making unreasonable permission demands upon installation.
(Source: BlackHatSecurity)
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the Web.

