There’s no doubt that, when jailbreaking an iPhone, iPad or iPod touch, you’re increasing the likelihood that said device will be susceptible to hacks and malware. The freedom offered by a jailbreak, particularly one of an untethered nature such as Evasi0n for iOS 7, is undeniable, but the obvious opportunity cost is that you’re less protected against threats. Case in point, a new piece of malware, discovered by Reddit users here and here, hibernates within the core folders of your iOS device, and worryingly, is able to swipe your Apple ID and password.
The malware, identified as Unflod.dylib, looks to have originated from China. Located in the DynamicLibraries folder (you can find it by browsing through /Library/MobileSubstrate/DynamicLibraries/Unflod.dylib on your own device), it listens out for any outgoing SSL connections, and when it manages to latch on to an Apple ID and password, the information is then relayed back to the creators of the malware in plain text.

Just how it finds itself on jailbroken devices, however, remains a mystery, which will be of great concern to users. One current theory is that dodgy, unofficial repositories containing unauthorized apps are infected with this particular piece of malware, but precisely which repo or app / tweak is currently unknown.
How to find out if you are infected by Unflod:
Naturally, you should avoid any repositories you don’t recognize, and if you are worried as to whether you may have an issue on your hands, you can check the location for that Unflod.dylib file as detailed by Saurik on Reddit here:
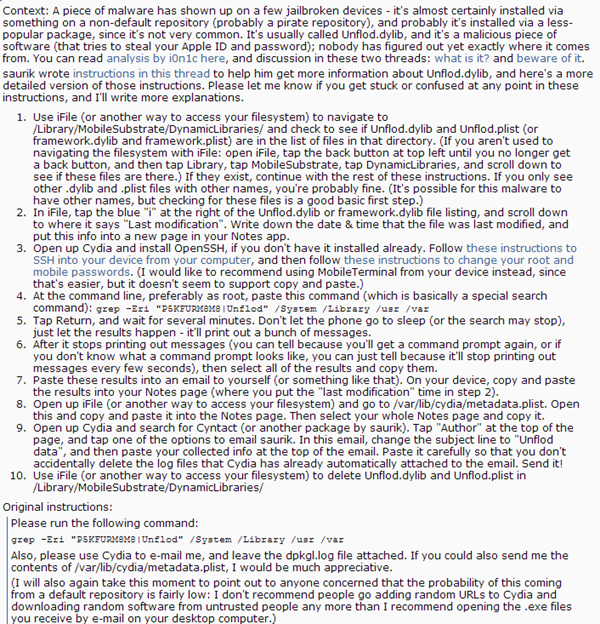
To do so, simply fire up your favorite file-browsing app (we recommend iFile), and navigate through /Library/MobileSubstrate/DynamicLibraries. If you happen to have this file named Unflod.dylib, then you are most likely infected.

How to remove the Unflod malware:
If you do happen to see the Unflod malware file in the above mentioned location, then be sure to delete it, and also, remove any tweaks, apps or repositories that you may have picked up from questionable sources.
Changing your Apple ID password would also be a good idea, but for good measure, those finding the Unflod.dylib file on their devices are encouraged to perform a full system restore. This will sacrifice the jailbreak, of course, but if you value your security enough, you’ll pay such a price to ensure that your sensitive information doesn’t fall into the wrong hands.
Outbreaks like this are very rare, even in the jailbreak community, but if there’s one thing to be learned here, it’s that sourcing apps from unspecified repositories can – on any mobile platform – put you at high risk of infection.
(source: SektionEins)
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the Web.

